What Everybody Ought To Know About How To Detect Man In The Middle Attack
Upguard named a leader for the 6th consecutive quarter by g2!
How to detect man in the middle attack. The intent is to appear as though the responses are among the two participants while the messages are actually being generated by the attacker. Email hijacking as its name implies, in this type of attack, cyber criminals take control of the email accounts of banks, financial institutions, or other trusted companies that have access to sensitive data—and money. Have you ever wondered if someone is trying to spoof your network to acquire confidential information?
Demo learn how cobalt’s pentest as a service (ptaas) model makes you faster, better, and more efficient. Attackers forcefully disconnect user sessions to intercept authentication information when the user tries to reconnect. Between you and your online banking;
Using a dummy access point with the same ssid and a stronger signal while disrupting the users’ traffic to the legitimate router; Or between your work emails and whoever is meant to send/receive them; Or between you and the box where you enter.
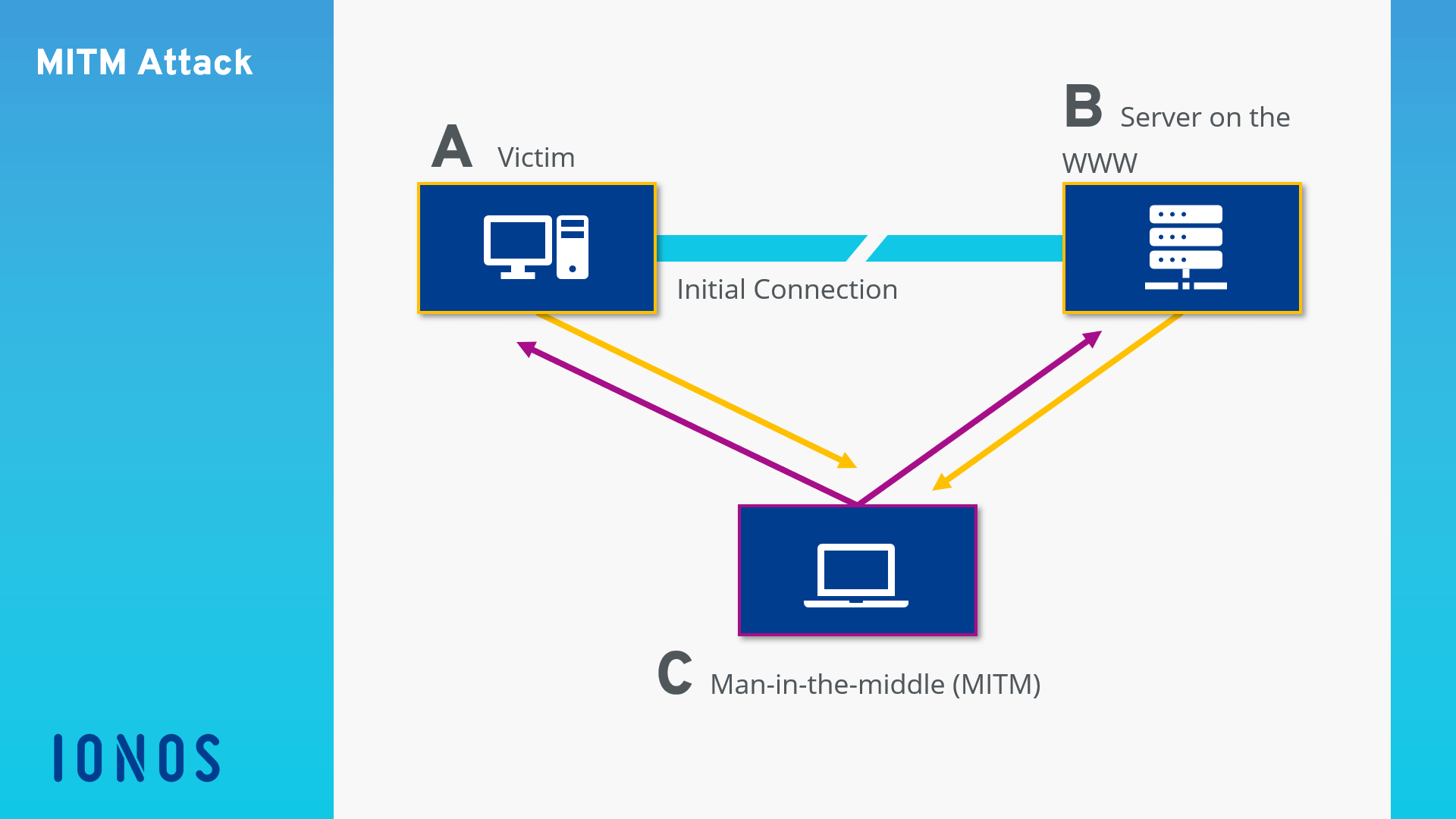
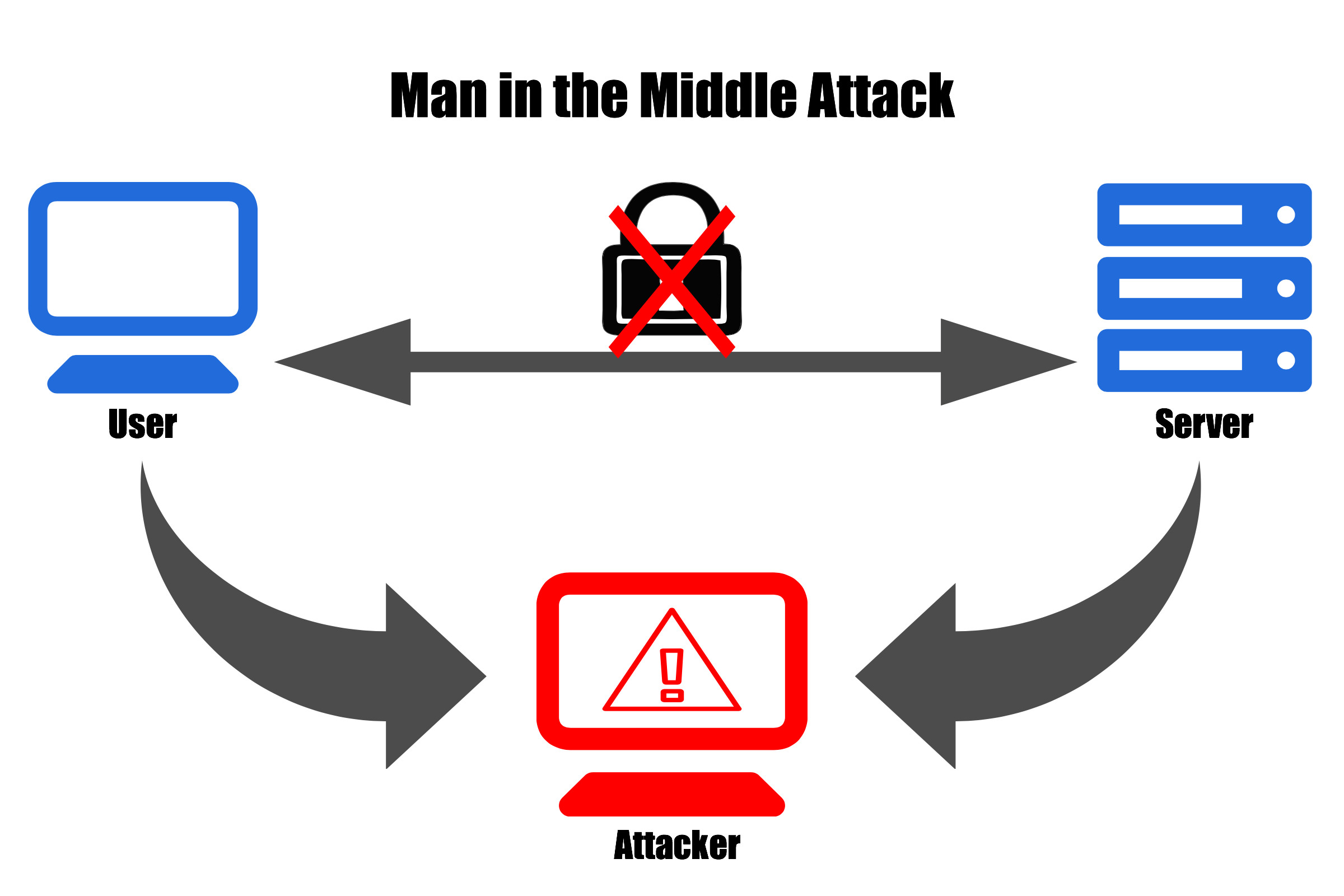
Once inside, attackers can monitor transactions and correspondence between the bank and its customers. In the interception phase, an attacker intercepts user traffic before it reaches the destination. Mitm attacks can happen in multiple ways, but the common denominator is a criminal intercepting some form of communication, rerouting the data to the attacker's desired destination, and then.
How to detect and prevent ‘man in the middle’ attacks | biztech magazine home » security oct 13 2023 security how to detect and prevent ‘man in the middle’ attacks mitm attacks have been around for years, but it leaders and users still must be wary of their hallmarks and practice good cyber hygiene to prevent them. He or she could then analyze and identify potentially useful information. Now we dive into how to best detect and prevent a mitm attack.
If the security measures are not sophisticated enough, they will not even detect man in the middle attack. It can be difficult to detect man in the middle attacks since the attackers hijack an active session. And so that it can be easily understood, it’s usually presented in the simplest iteration possible—usually in the context of a public wifi network.
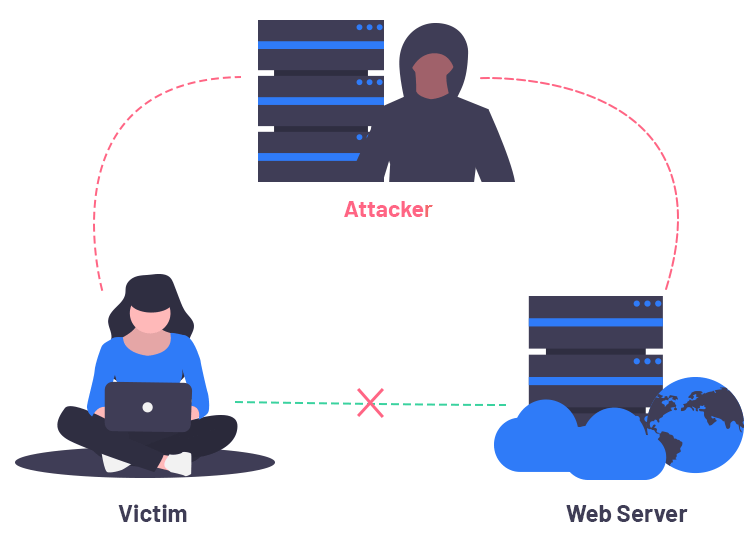
One of the most frequent mitm attack types, known as an “evil twin” attack, targets people who use free public wifi networks, such as those found in hotels, restaurants, airports, stores and other. The victim, the entity with which the victim is trying to communicate, and the “man in the middle” who’s intercepting the victim’s communications. However, monitoring certain parameters and observing network traffic can pinpoint an ongoing mitm attack, or intimate the sysadmins when a mitm attack was performed.
After inserting themselves in the middle of the transfer, the attackers pretend to be both legitimate participants. An attacker can log on and, using a free tool like wireshark, capture all packets sent between a network. The conventional wisdom is more prevention than detection.
Mitm attacks are essentially electronic.